If you are importing a wildcard certificate into the Fortigate that certificate request was likely generated on another Windows or Linux server and thus the private key resides there. If the wildcard certificate resides on a Windows server the certificate and private key will need to be exported (normally in pkcs12 format)
At this time the pkcs12 import feature on the Fortigate is broken and the .pfx file will need to be converted to PEM format using openssl. Once converted to PEM format the signed certificate and the private key will be copied into 2 separate files where they can be imported into the Fortigate.
Once imported into the fortigate that certificate will need to be specifically selected for the feature you are wanting it for. For SSL VPN it can be chosen form the GUI and for admin logon access it’s set via CLI:
#config system global #set admin-server-cert new_cert #end
Here are some step-by-step instructions on getting a cert exported from windows and imported into your Fortigate:
First open the Microsoft Management Console on your Windows Server:
Next add the Certificates snap-in:
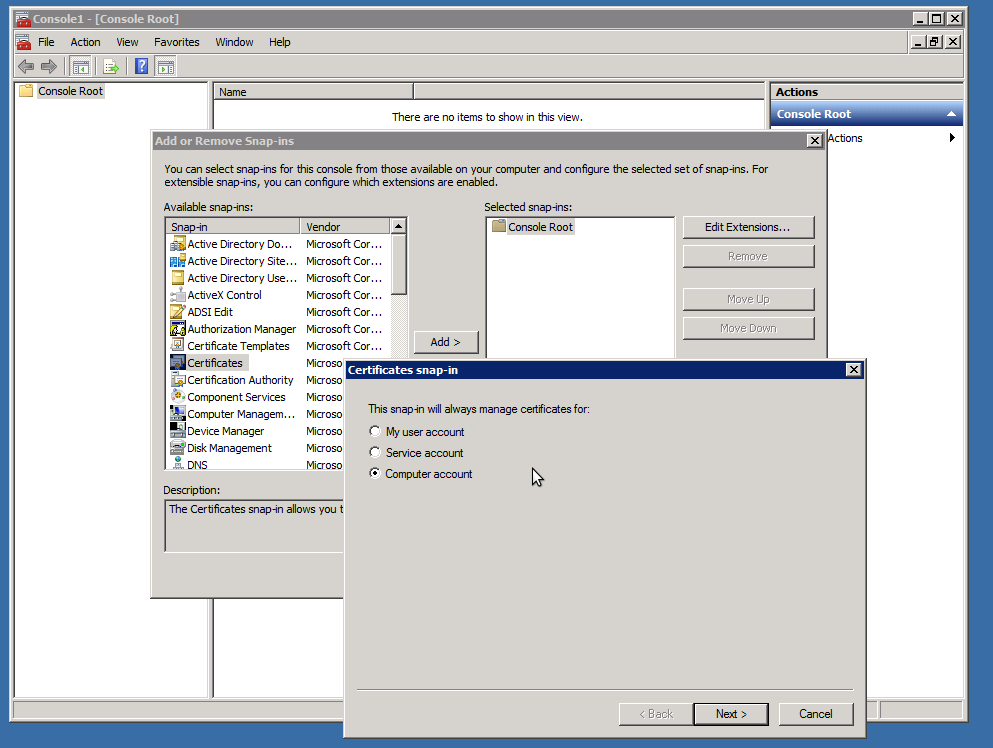
Now choose the certificate and export (with Private key):
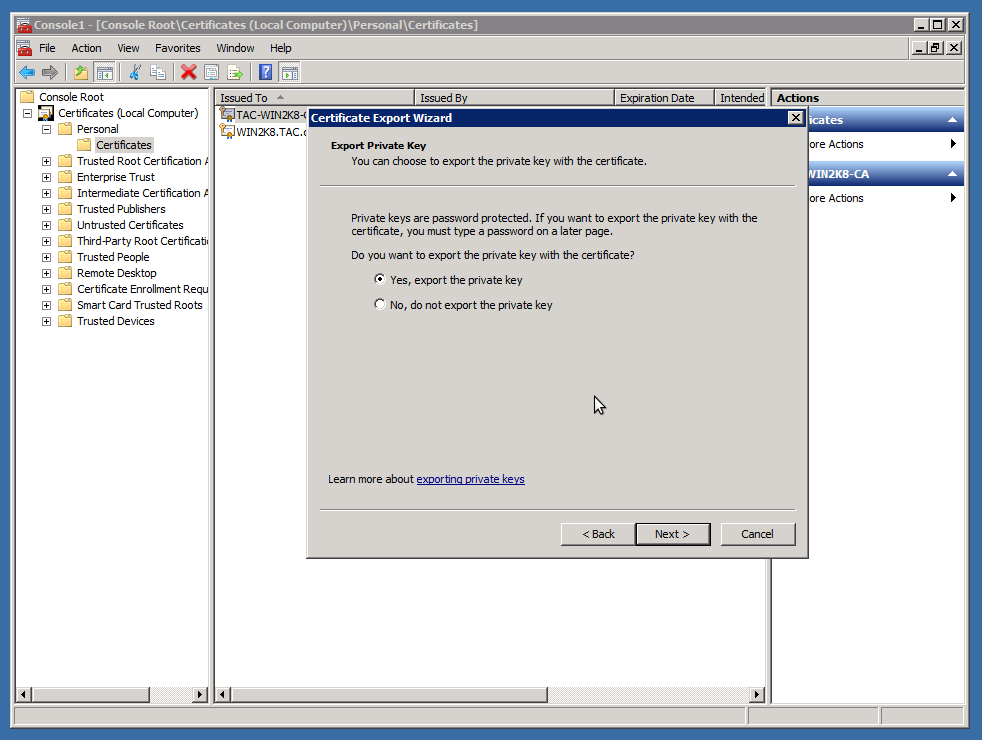
Now you’ll have a .pfx file that contains the signed certificate and the private key. We need to convert to PEM format using OpenSSL. OpenSSL for windows can be found here.
The following command will convert your pkcs12 certificate to PEM:
openssl pkcs12 -in example.pfx -out example.cer -nodes
You’ll now have a file which can be opened in a text editor (Wordpad is best here) We want to copy both the private and signed certificate into separate files which would look similar to the following:
private.key:
-----BEGIN PRIVATE KEY----- MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQDeFk/Te+EACmp9 TbFeGLxZz0lVowHh8X6m9gCn1J1FRewVhycwkmAx0TdhFMlFT0OJb0YKs461A2G7 PWfyiPvuEZhjHFy7xTlSJsfYZ8y+z2mok5t1S00hF4so9m02ZvPZ3G9oXyiBna4t ZmmrJboQ79quOqPTJ04b0TvgNlLKoPrDrJgX4Wm7ekpl07iLpL4kyxwz3m6l+xzu Dv35qKA6OXTo81QOIJKof/EKj5LpSVGxw8O1IzPE5zfQlwlIFc8WhkcYKVbxIwc1 ovtcfybIbnMBSFWutR9vCGrwWEQamsPNMlVAoKGeNcjpZ8pBI2a2tiRrOYOI2xUu Jxh4J5qrAgMBAAECggEBAIiD1IveQR+CR5VAlb+OmvDlz2FZswWNKdo9q4d+1THI 2mcdTgS4ZXMZ9N2zJkl5gL1Rbg+T8ivoqUGsbGIUvC/KFw8NVx+BC0wpVHz8yUmd O4iJO20tXXry+vKyD836GPkZXE4e+Eo8f92eb2Pp6+cPWS/yEdPw/D1zL0gSfG/a wLDissAqWxzmCFdM9fwtB3aSb5cJP3AL2NZ6ENqOtN96qGKjmXNRamjahGQQvfek 9U3lkmh0TFqIkcBHYZ9ywkfjxuZMaLh3UB7h/snojqkudpqLXq8nAg2ZS6QOKjz8 YnKWcdXN9WzGsOmU2FtbTIk9bYonDFWu+Z+ekVKYFvECgYEA/fsYVNJ3jF49PUPb XMG0ZZqjMmIexngLCoOF6cM+ptToxUVHyDJedKcPKEFXABbP89aXhl280UM0QJLv 65arEBjUfoJEeR5nfs3bhk5DjeI0o6lMTcmjtTmh0E7MpPZ5Nz78MKH8Ny0VUf9g gkv3k3eY57sqc3YzfRKqkO+87lkCgYEA39pObTt0e08pbsiaDXqMmRsvHLr5b/uW ZrQAxj+1FZPpNod2KoRuudWczUtOw5X6RCIWAKQT8Jlr+BFijJWCzofQYgNyjSAW n8H70n79IhFSoGHaghsCRTBAUlgFwe6qMR+6ngTLtKDtIg7OBOHfxCTweC1M4oE+ cm0rOJsvmKMCgYATgToQIY2uyPn4/4IUMIgTGXoY/3IPmd53MzyQhD8GfulVZQmr NTsNyFqgo8vzpMzZlAxU9FPw2jFkGCS2uf5vIQkIoiZyCsS190c5nD8R4WJbgz/p 5WdeHovvvG146bjLZlnlvjrpXdv6TRtzRjRALfofKb+L2HMB0vIoaVDgGQKBgAYz Do754Yz0sUoPJi0PYstutExQZU4ToqOvgoH7C7HQSdonwD8HMeXVo6UP29uQ0MCI TSGxaZf1N8dD+/22ukur+TptrAN6iwXbonS+7ZW+8xHcA+gshVCTOITPSUGIsY/w uANeUKHs/wQ9crkx5DeTalF5t7JiL++NVHAZ5CSPAoGAEX29UvDYKvbKLiGcM2zK r3ZuxUdxuKq0YaZxw9XR/Mhsbl0q1OwGrud/j4D71JmjTbSqPmT2sz4Owy1tyuqJ y2uVl6KYNnMVUYOCYQtSuFoWKZNuZN5wXoY0ztHzG0d5YE3zdKgpXaeGbKqgCHyA OSVt5g0hcZtNJUAilqVXePo= -----END PRIVATE KEY-----
And the signed cert, example.cer:
----BEGIN CERTIFICATE----- MIIC2jCCAcKgAwIBAgIQOhbovzAjwbJD/76oo0L4SzANBgkqhkiG9w0BAQUFADAW MRQwEgYDVQQDEwtGb3J0aU5pYy1QQzAeFw0xMjA0MTgxODM5NTJaFw0xMzA0MTgw MDAwMDBaMBYxFDASBgNVBAMTC0ZvcnRpTmljLVBDMIIBIjANBgkqhkiG9w0BAQEF AAOCAQ8AMIIBCgKCAQEA3hZP03vhAApqfU2xXhi8Wc9JVaMB4fF+pvYAp9SdRUXs FYcnMJJgMdE3YRTJRU9DiW9GCrOOtQNhuz1n8oj77hGYYxxcu8U5UibH2GfMvs9p qJObdUtNIReLKPZtNmbz2dxvaF8ogZ2uLWZpqyW6EO/arjqj0ydOG9E74DZSyqD6 w6yYF+Fpu3pKZdO4i6S+JMscM95upfsc7g79+aigOjl06PNUDiCSqH/xCo+S6UlR scPDtSMzxOc30JcJSBXPFoZHGClW8SMHNaL7XH8myG5zAUhVrrUfbwhq8FhEGprD zTJVQKChnjXI6WfKQSNmtrYkazmDiNsVLicYeCeaqwIDAQABoyQwIjALBgNVHQ8E BAMCBDAwEwYDVR0lBAwwCgYIKwYBBQUHAwEwDQYJKoZIhvcNAQEFBQADggEBACc6 JStV3v5XPq2jAsJojwB9uLnu3uMqp1n+mEnnbqTPHmodpCmaITbUQ6Bxf1MpTCX0 AUtEEDvfhX1IAonURNXGG6prEjKUIAF5Ww/EewhqDK1BcUdoCNu25P4Ty0SlTV4N gEQf0GbIxUZumf8SSyaSfcQOQLWARZP2RLbo15o9NkZpEZ+lq+sa1JjdF+U9fKcx IGRyAX5iUVylMDf3i5RiCio4+V0lUCV0c7ZyY+3Bgq9w6m1bgEdPD3XFTuXSDGKA dOxx7sAOVMJ49Eg89c9F8JKMykBP9lnhmnp//L9cMMqZp390HJmPxn0rcIhDvslo JOHMbSUaBBLcqSoTXZY= -----END CERTIFICATE-----
Now you can import both files into the Fortigate, Certificate type: Certificate. The password was removed during the conversion using OpenSSL so you won’t want to enter a password here.
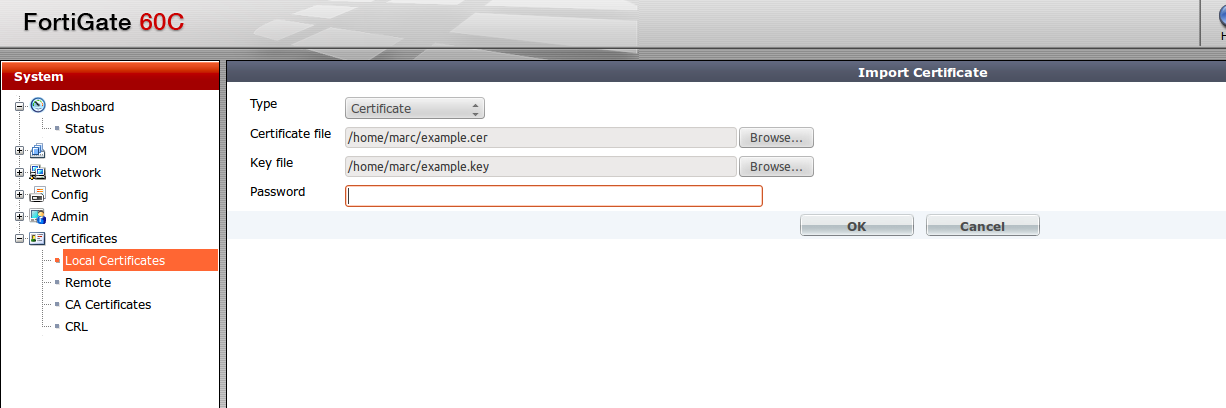
You should now have your certificate imported into the Fortigate and can begin using it.
