The following example uses OpenSSL to create your own CA (private and public keys) with which you can sign server and user certificates.
First make sure you have OpenSSL installed. I’m using OpenSSL in Ubuntu in this example.
First we are going to edit the OpenSSL config file to set default locations for certificates.
# vi /etc/ssl/openssl.cnf
You’ll want to make sure the certificates are placed in a good secure location so edit the following line:
dir = /root/CA_Cert [ policy_match ] countryName = optional stateOrProvinceName = optional organizationName = optional organizationalUnitName = optional commonName = supplied emailAddress = optional
Next make sure you have the appropriate directories created:
cd /root mkdir CA_Cert chmod 700 CA_Cert cd CA_Cert mkdir certs private newcerts
Create a serial file which will be used to name the new certificates generated and an index.txt file.
# echo 1000 > serial # touch index.txt
Now we create the CA private and public keys:
openssl req -new -x509 -days 3650 -keyout private/cakey.pem \ -out cacert.pem -config /etc/ssl/openssl.cnf
cakey.pem will always be kept secure and given to nobody, cacert.pem is the public key
If a certificate request was generated on the Fortigate and downloaded we can now sign it:
openssl ca -out SSLVPNCert.cer -infiles /root/Downloads/SSLVPNCert.csr
The SSLVPNCert.cer file will be imported back into the Fortigate and should be set as the certificate used as the server certificate under the SSL VPN Config section.
The cacert.pem file should also now be imported into users’ browsers under the Authorities section:
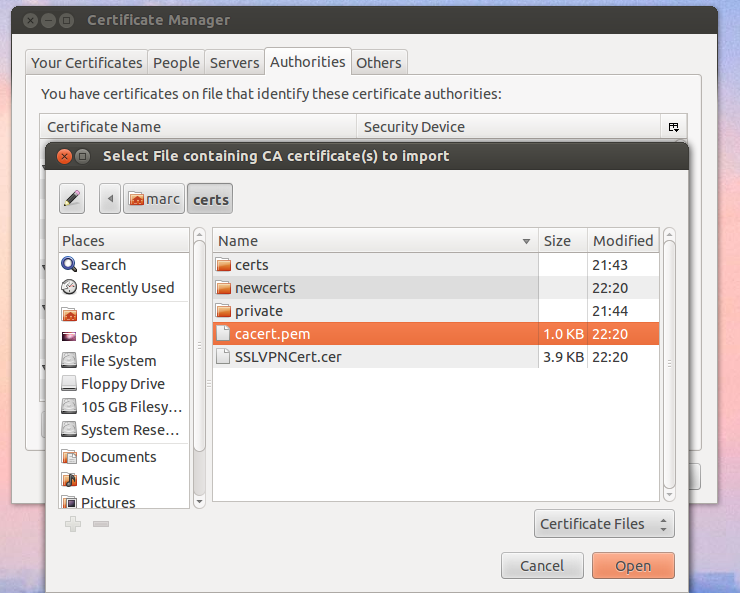
A quick test should reveal the SSL VPN login page now loads without warnings.
Next lets create the user certificate. First we generate a certificate request and private key:
openssl req -new -nodes -out clientcert.csr -keyout clientcert.key
Next we can sign the client certificate request using the ca key from earlier:
openssl ca -out clientcert.cer -infiles clientcert.csr
We can delete the certificate request (clientcert.csr), and we’ll need to export the public and private keys as a pkcs12 file:
openssl pkcs12 -export -out clientcert.pfx -inkey clientcert.key -in clientcert.cer
Next step is to import the .pfx into the users browser under the Personal/Your certificates section
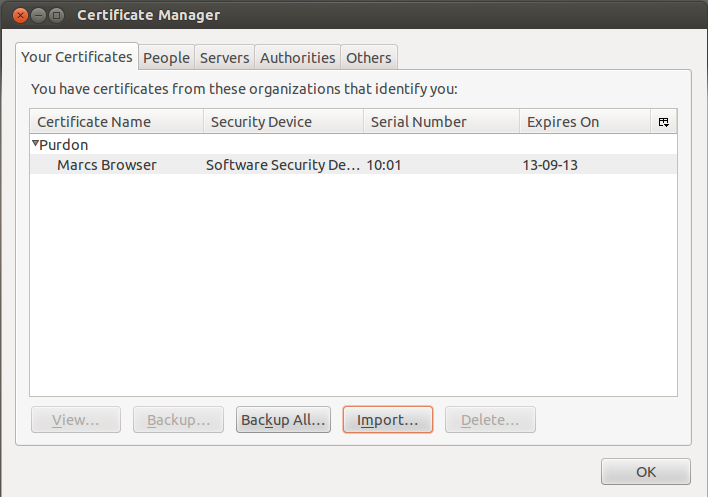
Now if you require the client certificate for SSL VPN access the browser will authenticate via it’s certificate. The cacert.pem file will also need to be imported into the Fortigate under the CA certificate section in order for the Fortigate to trust the certificate presented by the browser.
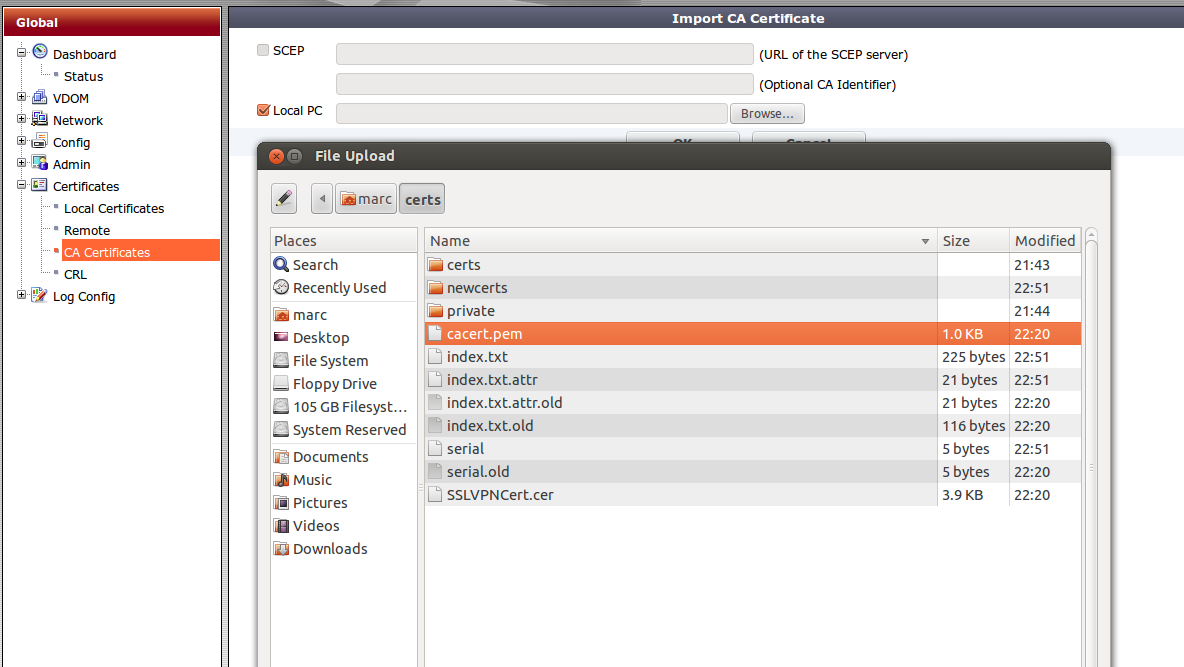
Another test should reveal that users can log into the SSL VPN using two-factor certificate/password authentication.
